Tổng hợp các lệnh Linux dùng để xử lý các vấn đề
Bài viết được sự cho phép của tác giả Lê Chí Dũng
1. List out all connections
The first and most simple command is to list out all the current connections. Simply run the netstat command with the a option.
$ netstat -a
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 enlightened:domain *:* LISTEN
tcp 0 0 localhost:ipp *:* LISTEN
tcp 0 0 enlightened.local:54750 li240-5.members.li:http ESTABLISHED
tcp 0 0 enlightened.local:49980 del01s07-in-f14.1:https ESTABLISHED
tcp6 0 0 ip6-localhost:ipp [::]:* LISTEN
udp 0 0 enlightened:domain *:*
udp 0 0 *:bootpc *:*
udp 0 0 enlightened.local:ntp *:*
udp 0 0 localhost:ntp *:*
udp 0 0 *:ntp *:*
udp 0 0 *:58570 *:*
udp 0 0 *:mdns *:*
udp 0 0 *:49459 *:*
udp6 0 0 fe80::216:36ff:fef8:ntp [::]:*
udp6 0 0 ip6-localhost:ntp [::]:*
udp6 0 0 [::]:ntp [::]:*
udp6 0 0 [::]:mdns [::]:*
udp6 0 0 [::]:63811 [::]:*
udp6 0 0 [::]:54952 [::]:*
Active UNIX domain sockets (servers and established)
Proto RefCnt Flags Type State I-Node Path
unix 2 [ ACC ] STREAM LISTENING 12403 @/tmp/dbus-IDgfj3UGXX
unix 2 [ ACC ] STREAM LISTENING 40202 @/dbus-vfs-daemon/socket-6nUC6CCxThe above command shows all connections from different protocols like tcp, udp and unix sockets. However this is not quite useful. Administrators often want to pick out specific connections based on protocols or port numbers for example.
2. List only TCP or UDP connections
To list out only tcp connections use the t options.
$ netstat -at
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 enlightened:domain *:* LISTEN
tcp 0 0 localhost:ipp *:* LISTEN
tcp 0 0 enlightened.local:36310 del01s07-in-f24.1:https ESTABLISHED
tcp 0 0 enlightened.local:45038 a96-17-181-10.depl:http ESTABLISHED
tcp 0 0 enlightened.local:37892 ABTS-North-Static-:http ESTABLISHED
.....Similarly to list out only udp connections use the u option.
$ netstat -au
The above output shows both ipv4 and ipv6 connections.
3. Disable reverse dns lookup for faster output
By default, the netstat command tries to find out the hostname of each ip address in the connection by doing a reverse dns lookup. This slows down the output. If you do not need to know the host name and just the ip address is sufficient then suppress the hostname lookup with the n option.
$ netstat -ant
The above command shows ALL TCP connections with NO dns resolution. Got it ? Good.
4. List out only listening connections
Any network daemon/service keeps an open port to listen for incoming connections. These too are like socket connections and are listed out by netstat. To view only listening ports use the l options.
$ netstat -tnl
Now we can see only listening tcp ports/connections. If you want to see all listening ports, remove the t option. If you want to see only listening udp ports use the u option instead of t.
Make sure to remove the ‘a’ option, otherwise all connections would get listed and not just the listening connections.
5. Get process name/pid and user id
When viewing the open/listening ports and connections, its often useful to know the process name/pid which has opened that port or connection. For example the Apache httpd server opens port 80. So if you want to check whether any http server is running or not, or which http server is running, apache or nginx, then track down the process name.
The process details are made available by the ‘p’ option.
~$ sudo netstat -nlpt
When using the p option, netstat must be run with root privileges, otherwise it cannot detect the pids of processes running with root privileges and most services like http and ftp often run with root privileges.
Along with process name/pid its even more useful to get the username/uid owning that particular process. Use the e option along with the p option to get the username too.
$ sudo netstat -ltpe
The above example lists out Listening connections of Tcp type with Process information and Extended information.
The extended information contains the username and inode of the process. This is a useful command for network administrators.
Note – If you use the n option with the e option, the uid would be listed and not the username.
6. Print statistics
The netstat command can also print out network statistics like total number of packets received and transmitted by protocol type and so on.
To list out statistics of all packet types
$ netstat -s
To print out statistics of only select protocols like TCP or UDP use the corresponding options like t and u along with the s option. Simple!
7. Display kernel routing information
The kernel routing information can be printed with the r option. It is the same output as given by the route command. We also use the n option to disable the hostname lookup.
$ netstat -rn
8. Print network interfaces
The netstat command can also print out the information about the network interfaces. The i option does the task.
$ netstat -i
The above output contains information in a very raw format. To get a more human friendly version of the output use the e option along with i.
$ netstat -ie
The above output is similar to the output shown by the ifconfig command.
9. Get netstat output continuously
Netstat can output connection information continuously with the c option.
$ netstat -ct
The above command will output tcp connections continuously.
10. Display multicast group information
The g option will display the multicast group information for IPv4 and IPv6 protocols.
$ netstat -g
More examples of netstat command
Okay, we covered the basic examples of netstat command above. Now its time to do some geek stuff with style.
Print active connections
Active socket connections are in “ESTABLISHED” state. So to get all current active connections use netstat with grep as follows
$ netstat -atnp | grep ESTA
To watch a continous list of active connections, use the watch command along with netstat and grep
$ watch -d -n0 "netstat -atnp | grep ESTA"
Check if a service is running
If you want to check if a server like http,smtp or ntp is running or not, use grep again.
$ sudo netstat -aple | grep ntp
So we found that ntp server is running. Grep for http or smtp or whatever you are looking for.
Well, that was most of what netstat is used for. If you are looking for more advanced information or want to dig deeper, read up the netstat manual (man netstat).
And do leave your feedback and suggestions in the comments box below.
So sánh command line system
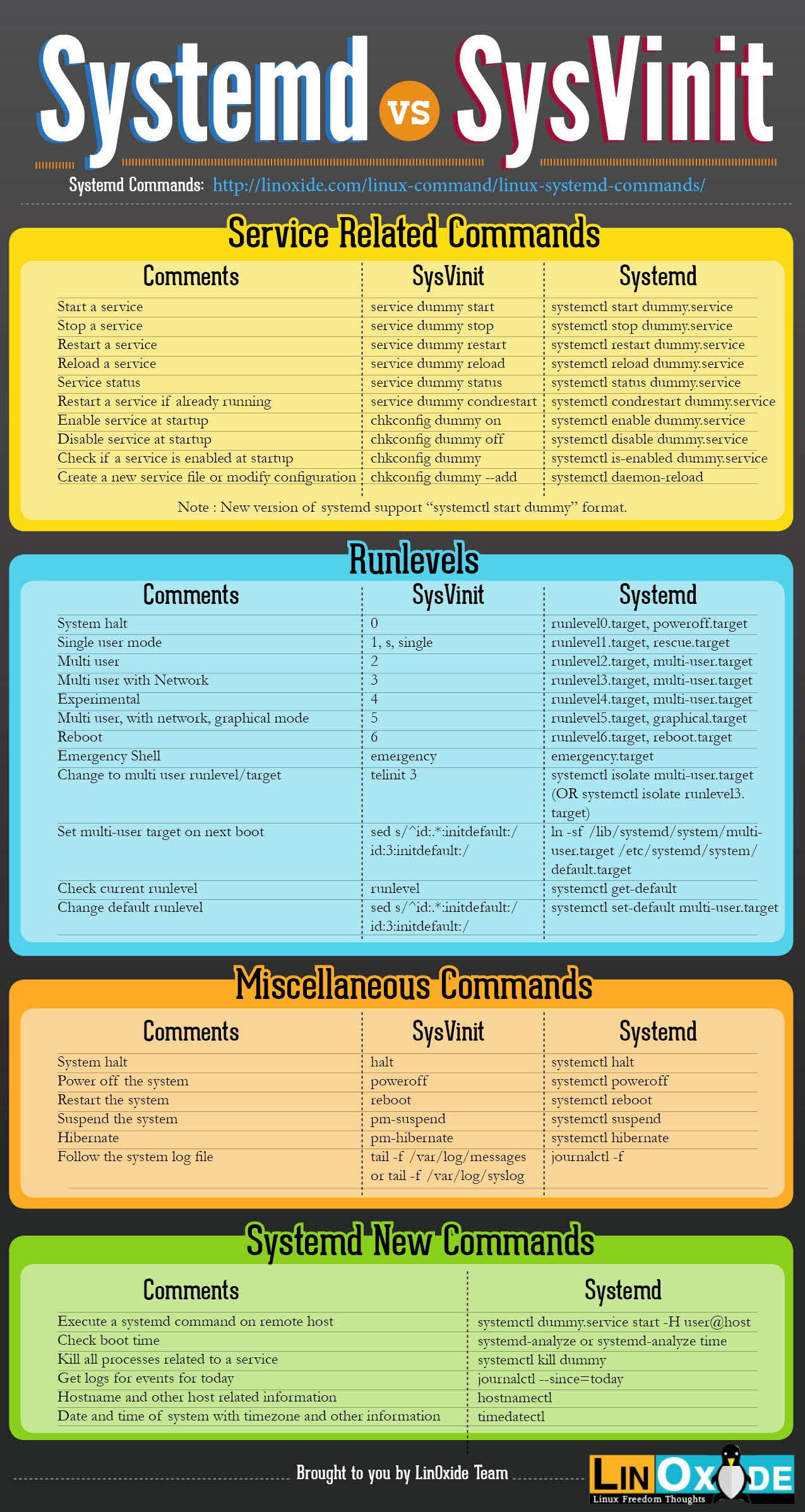
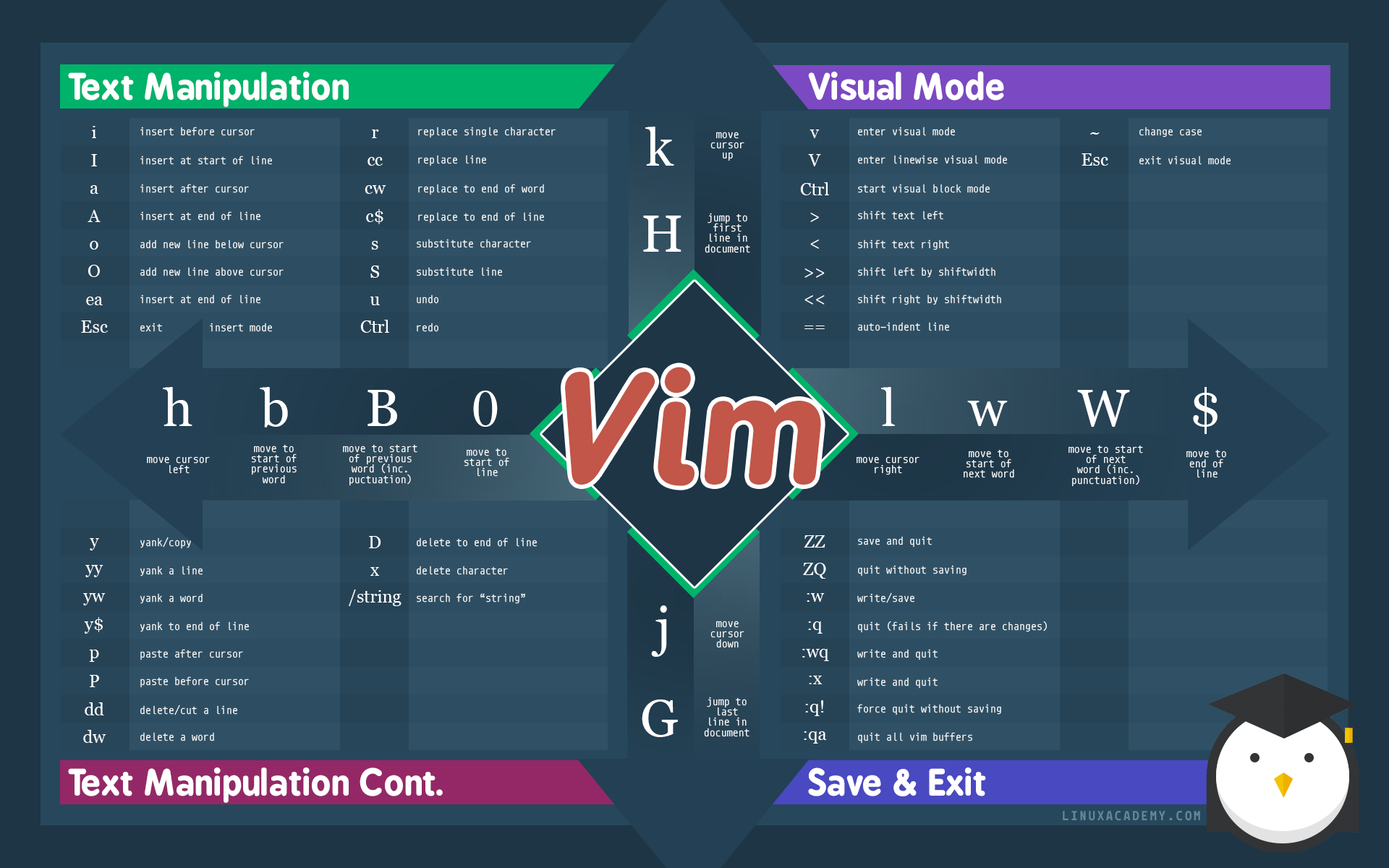
Các lệnh sử dụng Vim trên system
Rsync
rsync -a ~/dir1 username@remote_host:destination_directory
Có thể bạn quan tâm:
- Cài đặt Rust trên Arch Linux
- Chuyện gõ tiếng Việt trên Linux
- Top câu hỏi phỏng vấn Linux hàng đầu dành cho ứng viên
- T Thoughtworks: Nơi công nghệ chạm đích đến
- Đ Đại dương xanh cho Doanh nghiệp tăng trưởng bền vững trên Zalo
- L Lakehouse Architecture: Nền tảng dữ liệu cho ứng dụng AI trong tương lai
- G Giải Quyết Bài Toán Kinh Doanh Bằng Big Data và AI
- B BenQ RD Series – Dòng Màn Hình Lập Trình 4k+ Đầu Tiên Trên Thế Giới
- F Framework nào tốt nhất cho dự án của bạn? – Checklist chi tiết
- K Kinh nghiệm xử lý responsive table hiệu quả
- S Stackoverflow là gì? Bí kíp tận dụng Stack Overflow hiệu quả
- 7 7 kinh nghiệm hữu ích khi làm việc với GIT trong dự án
- B Bài tập Python từ cơ bản đến nâng cao (có lời giải)